Search
Explore digital transformation resources.
Uncover insights, best practises and case studies.
Search
Explore digital transformation resources.
Uncover insights, best practises and case studies.
Given the increasing threats in today’s digital landscape, sticking to outdated development practices is no longer an option. Adopting the DevSecOps approach is essential for modern software development, as it prioritizes security as an integral part of the process. The real challenge, however, lies in effectively navigating the transition from traditional methods to a robust DevSecOps framework. Embracing this change is crucial for building secure and reliable software systems.
Service
The discovery of a major vulnerability in the popular Log4j logging software, reported in November 2021, sent shockwaves through the tech community. This flaw, known as Log4Shell, allowed hackers to take control of systems remotely and had the potential to affect hundreds of millions of devices. This led to a mad scramble to fix affected systems. This incident was a stark reminder of the importance of integrating security at every stage of software development, even for a simple logging framework.
Enter DevSecOps (Development, Security, and Operations), a modern approach that blends security seamlessly into the development and operations process. By making security everyone’s responsibility, DevSecOps helps teams discover and fix vulnerabilities early, long before they become a threat. A key part of this strategy is known as “shift-left security,” which means addressing security issues right from the start, rather than waiting until the end of the development cycle.
If organizations using Log4j had employed DevSecOps and shift-left security, they could have detected the Log4Shell vulnerability much earlier, avoiding the last-minute scramble to patch systems. By using automated tools to check code and proactively model potential threats continuously, DevSecOps makes it easier to build secure software from the ground up.
In traditional software development, security is often considered late in the process, sometimes even after the software is ready for deployment. This can lead to discovering critical vulnerabilities at the last minute, subsequent delays, and increased costs.
Instead of treating security as a separate step, DevSecOps ensures that security is a fundamental part of the entire process – from the initial design to the final deployment.
By embedding security from the beginning into every stage of the software development lifecycle, DevSecOps between developers, security experts, and operations teams. This collaboration ensures that security vulnerabilities are identified and addressed early, reducing risks and costs associated with late-stage fixes. It fosters shared responsibility, enabling faster, more secure software delivery while maintaining operational efficiency.
By automating repetitive tasks and integrating security tools into the development pipeline, teams can work more efficiently and catch potential issues early.
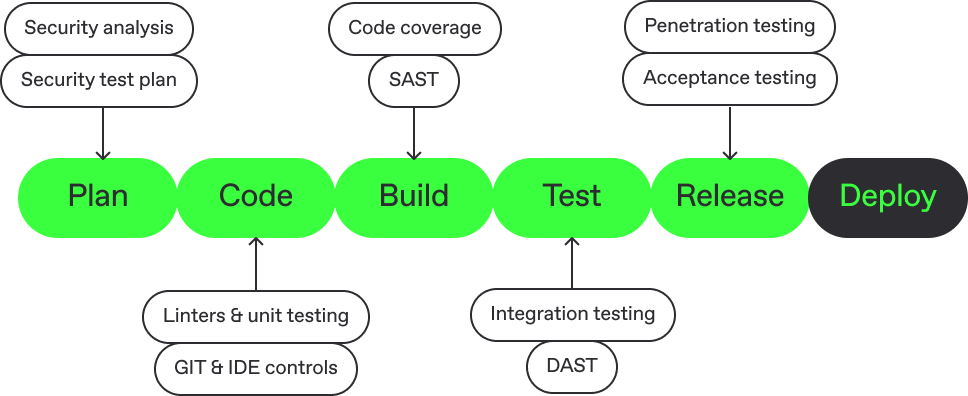
The shift-left approach pushes security even further upstream. It’s about thinking of security from the moment you start designing the software, not just when you’re ready to launch. This means, for example, doing threat modeling in the planning and design phase, carrying out SAST during coding and DAST during testing, and performing penetration tests in deployment. This way, potential security issues are identified and resolved early, reducing the risk of expensive fixes down the road.

In the world of software security, there are several common vulnerabilities that developers need to watch out for. Letting vulnerability develop into an actual threat can lead to serious consequences such as security breaches, data loss or theft, legal and regulatory penalties, increased development costs, and loss of business reputation. DevSecOps can easily address some of the most prevalent ones. Fortunately, we have many security tools at our disposal to keep our software safe.
SQL injection: This occurs when attackers insert malicious SQL code into a query, potentially allowing them to access or manipulate the database. Static Application Security Testing (SAST) tools can help detect SQL injection vulnerabilities during the coding phase, while Dynamic Application Security Testing (DAST) tools can identify them in the running application.
Cross-site scripting (XSS): XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by legitimate users – for example, a script that steals your money while you view your bank account. SAST tools can catch these issues in the code, and DAST tools can find them in the live application.
Buffer overflows: Buffer overflows happen when a program writes more data to a buffer than it can hold, leading to crashes or code execution by attackers. SAST tools are particularly effective at identifying buffer overflow vulnerabilities early in development.
Insecure deserialization: This vulnerability occurs when untrusted data is used to reconstruct objects, leading to potential code execution. Both SAST and Interactive Application Security Testing (IAST) tools can help detect insecure deserialization issues.
Security misconfigurations: These occur when applications, servers, or databases are not configured securely, leaving them open to attacks. DAST tools are well-suited to find security misconfigurations in running applications, while automated configuration management tools can help prevent these issues in the first place.
By using DevSecOps practices and tools, teams can identify and fix these vulnerabilities early, reducing the risk of security breaches.
With the rise of containerized applications, securing containers has become a critical part of DevSecOps. Containers allow developers to package applications and their dependencies into a single, portable unit that can run anywhere. However, this convenience comes with its own set of security challenges.
By incorporating these techniques into their DevSecOps practices, organizations can better secure their containerized environments and reduce the risk of attacks.
The shift-left philosophy in DevSecOps emphasizes integrating security earlier in the software development lifecycle, fostering a proactive rather than reactive approach to protecting applications. By embedding security practices into every development phase, teams can identify and address vulnerabilities before they become critical.
This alignment empowers developers with the tools and knowledge to build secure code and streamlines collaboration between development, operations, and security teams. Automation and proactive risk assessment further enhance the effectiveness of this approach, enabling faster and more secure delivery of software. Together, these elements create a culture where security becomes an integral part of development rather than an afterthought.
To successfully implement a shift-left security approach and keep your code safe, there are three key things to remember: recognition and collaboration among developers, proactive security risk identification, and using automation as a tool.
Educating developers on security: One of the most important steps in implementing shift-left security is educating developers about best practices. Developers need to understand the basics of secure coding, be aware of common vulnerabilities, and stay informed about the latest security threats. This can be achieved through workshops, online courses, and certification programs. Additionally, integrating security training into the onboarding process for new hires ensures that everyone starts with a strong foundation.
Regular training sessions and refresher courses are also essential, as the world of cybersecurity is constantly evolving. Developers should be encouraged to stay curious and keep learning new techniques and tools to help them build more secure software.
Automating security testing: Automated security testing is crucial for maintaining security throughout the development lifecycle. By integrating tools like Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Interactive Application Security Testing (IAST) into the development pipeline, organizations can ensure that security checks are performed automatically with every code change.
By automating these processes, teams can quickly detect and address security issues without slowing development.
Proactive threat modeling: Threat modeling is a proactive strategy that involves identifying potential security threats during the design phase of a project. This process helps developers understand the security implications of their design decisions and allows them to build more secure systems from the ground up.
Key steps in threat modeling include:
Tools like Microsoft Threat Modeling Tool and OWASP Threat Dragon can assist in this process, making it easier for teams to visualize and address potential threats.
Collaborative code reviews and pair programming: Code reviews and pair programming are collaborative practices that can significantly enhance the security of the codebase. In a code review, one or more developers examine another developer’s code for security vulnerabilities, coding errors, and adherence to best practices. This peer review process helps identify issues that automated tools might miss and promotes knowledge sharing among team members.
Pair programming takes this collaboration a step further by having two developers work together at the same workstation – one writes code while the other reviews it in real-time. This method improves code quality and fosters a culture of collaboration and continuous learning. Both practices encourage developers to think critically about security and quality while writing and reviewing code.
Implementing DevSecOps and shift-left security practices can be challenging, especially for organizations that are used to more traditional approaches, as it involves changes related to people, processes, and tools.
Moving to a DevSecOps approach requires a cultural shift, which can face significant resistance. Many organizations are accustomed to a siloed approach where development, operations, and security teams operate independently. Overcoming this resistance involves leadership support, continuous education, and clear communication about the benefits of DevSecOps and shift-left security.
Developers and operations teams may also lack the necessary security knowledge creating skill gaps and necessitating extensive training. Security expertise is often concentrated within a specialized team, which can create bottlenecks. Bridging this gap requires investment in training programs that focus on secure coding practices, threat modeling, and security tools.
Integrating new security tools into existing workflows can be challenging. Many organizations have established development pipelines, and introducing new tools can disrupt these processes. Choosing tools that integrate seamlessly with existing CI/CD pipelines and development environments is essential.
Implementing DevSecOps and shift-left security practices requires time, effort, and financial resources. Smaller organizations or teams may struggle with limited budgets and staffing. Prioritizing high-impact areas and starting with incremental changes can help manage resources effectively.
Start small. Begin by automating security testing for critical components and gradually extend it to the entire codebase. This allows teams to adapt and refine processes incrementally, reducing the risk of major disruptions.
Learn continuously. Regular training and workshops ensure that development teams stay updated on the latest security practices. Encourage a culture of continuous learning by providing access to online courses, certifications, and industry conferences.
Foster collaboration. DevSecOps thrives on collaboration. Encourage cross-functional teams to work together and break down silos. Implement practices like pair programming, where developers work together and review each other’s code in real-time.
Automate security processes. Use tools like SAST, DAST, IAST, and container security scanners to integrate security checks into the CI/CD pipeline. Automation helps in early detection and remediation of vulnerabilities, reducing the burden on security teams and allowing developers to focus on building secure code.
Involve security early. Involve security teams early in the development process, from the design phase to deployment. Early involvement helps identify potential security issues before they become critical, allowing for proactive measures rather than reactive fixes.
The Log4j vulnerability was a wake-up call for the tech industry, emphasizing the importance of integrating security at every stage of development. By embracing DevSecOps and the shift-left security paradigm, organizations can detect and mitigate vulnerabilities early, reducing costs and enhancing overall security. With the right tools, training, and cultural mindset, businesses can build more secure software, deliver it faster, and ensure that security is a shared responsibility across all teams.
Nortal is a strategic innovation and technology company with an unparalleled track-record of delivering successful transformation projects over 20 years.